If you’ve ever worked in environments requiring a proxy, reverse proxy, or caching system, you’ve likely heard of Squid proxy. Squid is one of the leading open-source proxy tools with an extensive community and available plugin library. As is the case with many large, open source projects, there are many different ways to accomplish a […]
Owning SAML
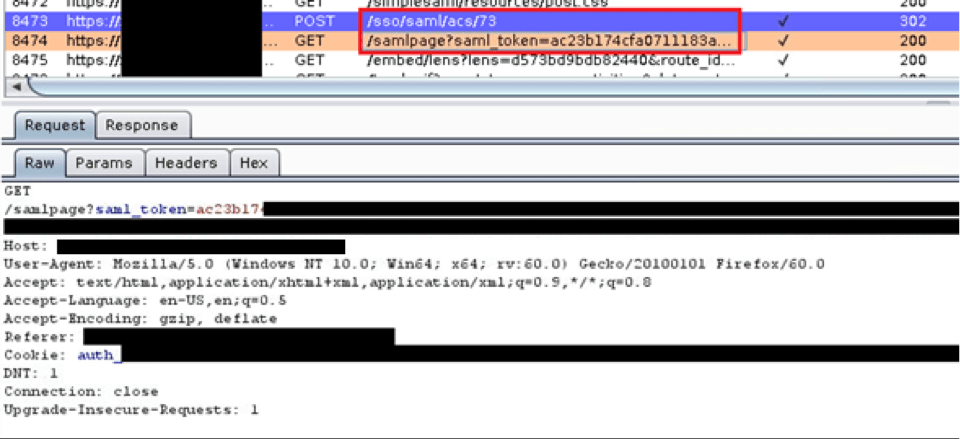
Exploiting a SAML Implementation and SAML Vulnerability During a recent web application test, I discovered a bug in a Security Assertion Markup Language (SAML) implementation. This bug involved an insecure implementation of a SAML feature combined with a custom authentication mechanism our client developed out of a need to support their customers. With a bit […]
A Study in Exploit Development – Part 2: Taking it to the Next Level
Welcome to Part 2 of this 2-part blog series looking at the details of exploring and validating an exploit! If you liked this series, I bet you’d be interested in our webinar on How to Think Like A Hacker, check it out! Now on to Part 2: Taking it to the Next Level. (Part 1 […]
A Study in Exploit Development – Part 1: Setup and Proof of Concept
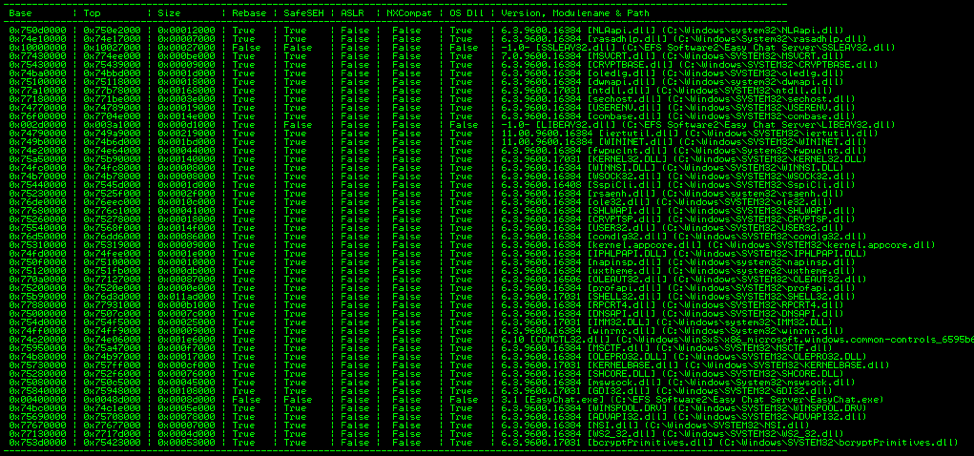
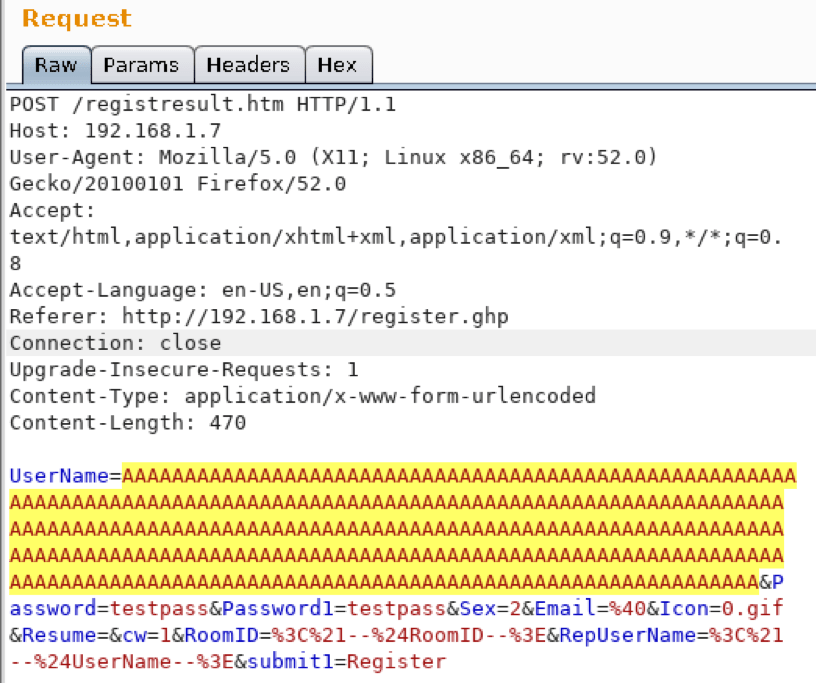
A Study in Exploit Development: Easychat SEH exploit A typical penetration test involves automated compliance scanning to identify vulnerabilities, followed by a more manual testing process where the tester attempts to validate and exploit those vulnerabilities. Many times, we discover vulnerabilities with publicly available exploits. This can sometimes result in a complete domain compromise. Other […]
PCI 3.0 Secure Authentication Requirement
The new PCI 3.0 introduces a subtle, but important new requirement for addressing security authentication and session management for web applications.
Is badBIOS for Real?
Is badBIOS a real threat? Maybe not, but the origin of this threat could be a very real problem.