All Posts
October 14, 2024
Introducing FedRAMP Insights on the Azure Marketplace: Accelerating FedRAMP Compliance with Automated Precision
We are excited to announce the launch of FedRAMP Insights, now available in the Azure Marketplace. This innovative tool is designed…
November 22, 2023
Seeking SaaS: FedRAMP Launches Modernization and 10X Increase
At the end of October, the federal Office of Management and Budget (OMB) released a draft memorandum for public comment titled…
October 25, 2023
Ripcord Transforms, Anitian Empowers, Agencies Win
As far back as 2011 a presidential mandate said, “Records are the foundation of open government.” This mandate went on to…
August 22, 2023
Revving Up for Rev5, Part 3: Recommendations and Timelines
FedRAMP R5 represents a lot of change. So much change that we can’t track it all in this one blog, though we gave…
August 1, 2023
Revving Up for Rev5, Part 2: SCRM, Privacy and Encryption
In Part 1 of this three-part blog series we provided an overview of FedRAMP Rev5 changes: why they came about, what they aim…
July 5, 2023
Revving Up for Rev5: When Threats Evolve, FedRAMP Must Evolve
It’s been a tough couple of years for cybersecurity strategists and practitioners. In 2021, supply chain attacks on Kaseya, Solar Winds, Accellion and other hardware…
December 20, 2022
Tips & Best Practices for Configuring Squid with NTLM Authentication
If you’ve ever worked in environments requiring a proxy, reverse proxy, or caching system, you’ve likely heard of Squid proxy. Squid…
November 15, 2022
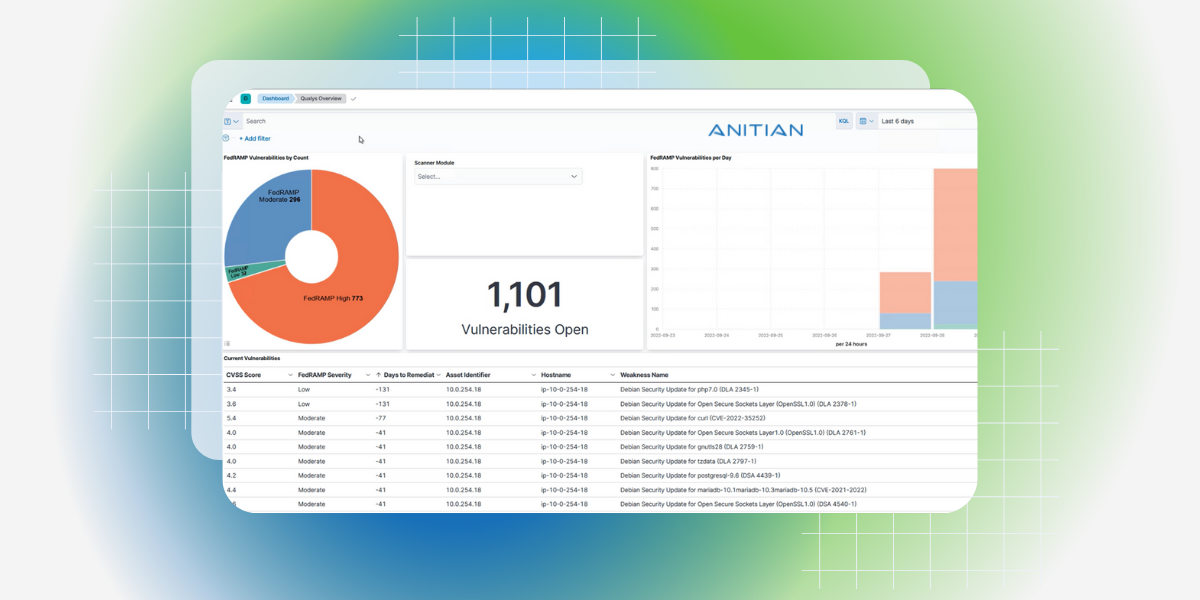
Anitian Makes it Easier to Find & Fix Vulnerabilities with New FedRAMP Dashboard
Today we’re excited to announce Anitian’s new interactive Vulnerability Management Dashboard which provides SecOps teams with a unified view of all…
October 27, 2022
Anitian Named Finalist in Black Unicorn Awards for 2022
Company recognized as a finalist in the Baby Black Unicorn category, having potential of being valued at $1B in near future….
August 24, 2022
Anitian Named a Sample Vendor in Three Gartner Hype Cycle Reports
Company included in Hype Cycle for Agile and DevOps, Hype Cycle for I&O Automation, and Hype Cycle for Cyber Risk Management. …
August 19, 2022
Debunking Quantum Cloud Myths
In many ways, the human appetite for computing power is ever-growing. More computing power can be found in the cloud for…
July 18, 2022
Anitian Expands Leadership Team with Appointment of CMO and CRO to Fuel Next Stages of Growth
Positioning for the next wave of growth, Maria Crawford and Tom Pak bring a combined 40 years of marketing and sales…
June 21, 2022
The Post-COVID Cloud Boom Report: A Deep Dive
In this episode of the Security on Cloud Podcast, we’re joined by Dr. Larry Ponemon, the Chairman and Founder of the…
June 6, 2022
Anitian Wins Nine Global InfoSec Awards at RSA Conference 2022
Anitian named top cybersecurity company in an astounding nine categories, including Hot Company Security Company of the Year, Most Comprehensive Compliance,…
May 10, 2022
Security Advocacy in the Cloud with Jacob Ansari from Schellman
In this episode, we talk with Jacob Ansari, a Security Advocate at Schellman, who leads the firm’s security best practices advocacy….
May 5, 2022
Anitian and Ponemon Release New Post-COVID Cloud Boom Study That Reveals How Enterprise Digital Transformation Significantly Increased Business Growth, Security Posture, and Financial Strength
Sponsored by Anitian, Ponemon Institute's The Post-COVID Cloud Boom breaks down how COVID-19 changed the migration of applications to public cloud…