The National Institute of Standards and Technology (NIST) recently released the first public draft of NIST 800-53 revision 5, Security and Privacy Controls for Information Systems and Organizations. This is the first updated to this massive standard in over five years. NIST 800-53 is a 500 page standard for security controls.
While many of the actual standards are the same, some of the changes are quite dramatic. We have a quick summary of the changes.
New Voice
Perhaps the most notable change is the voice of the document. This change is absolute music to our ears at Anitian. Maybe they read our blog I Am Not Reading Your Security Policy. Gone from 800-53 is the third party, indirect language which is extremely difficult to read and understand. Replacing that is more direct, action-oriented words.
Consider this change for Access Control 6 (AC-06) that deals with least privilege:
Rev. 4: The organization employs the principle of least privilege, allowing only authorized accesses for users (or processes acting on behalf of users) which are necessary to accomplish assigned tasks in accordance with organizational missions and business functions.
Rev. 5: Employ the principle of least privilege, allowing only authorized accesses for users (or processes acting on behalf of users) which are necessary to accomplish assigned tasks in accordance with organizational missions and business functions.
Notice that the use of the third-party construct of “the organization” is gone. Rather, the sentence begins with “Employ” changing it to an imperative statement.
This may seem small, but multiply this change across more than 300 controls and control enhancements and what you get is a much easier to read and understand standard.
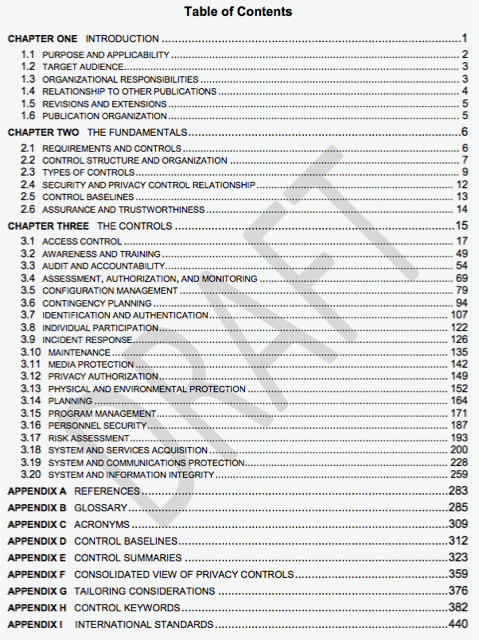
Even the table of contents is significantly more user-friendly. Compare the images below and think for a moment about which document you’d rather navigate to find the risk assessment controls family:
Figure 1: NIST 800-53 revision 4 Table of Contents
Figure 2: NIST 800-53 revision 5 Table of Contents
Control Set Moved
In revision 4, the control set, arguably the most important part of the document, did not begin until Appendix F. Revision 5 now starts the control families on page 15. This makes a lot more sense. It gets to the important content faster.
Moreover, it is important to remember, that 800-53 is fundamentally a control standard. It is not like ISO 27001 or NIST Cybersecurity Framework, which are security program standards. This is another welcome change to not have to wade through 90 pages of exposition to get to the actual controls!
Selection Guidance
Another welcome change is the migration of control selection guidance from 800-53 to 800-37. Control selection is the process of determining which controls should be included to protect a given system or organization. This should be a risk based process. 800-37, titled the “Guide for Applying the Risk Management Framework to Federal Information Systems” is a risk management process. So this is a good change that also makes a lot of sense.
There is a good chance the title of 800-37 will change to reflect both its new role and the shift towards general applicability, as opposed to being solely intended for the US government. This is another example of NIST aligning with ISO 27001, which also uses risk assessment as the mechanism for defining one’s control set (in spite of the fact that ISO does provide a control set, it is only guidance, as we discussed in Part 2 of our recent ISO blog series).
Privacy Front and Center
Here is an interesting change, that shows some clear intent. Privacy risks have moved forward in the text. Privacy is now called out specifically in the supplemental guidance of each control that affects the identifiability of individuals. That better reflects the times, as regulations around privacy have solidified in the last few years. It also makes it easier to assess a control’s value to an organization handling PII. Again, NIST is showing greater awareness and alignment with international standards, such as GDPR, as well as other US standards such as GLBA and HIPAA, all of which deal with a form of PII.
Conclusion
Having written a Federal System Security Plan (SSP) under the guidelines in 800-53 r4, this Revision 5 is a huge improvement. We believe it will aid in adoption. Readability really matters and revision 5 makes huge steps forward.
You can get your own copy of NIST 800-53 here. And best of all the NIST documents are free of charge. Which is not true of the ISO 27000 series. Those documents will set you back about $1,200 per copy!
NIST will accept comments on 800-53 Rev 5 through September 15th. If you have any feedback for them, email sec-cert@nist.gov.