President Joe Biden signed and released an Executive Order (EO) from the White House on May 12th, addressing his plan to improve the nation’s cybersecurity and protect federal government networks. This order comes on the heels of the Colonial Pipeline Ransomware attack and the now infamous SolarWinds breach. You can read the full text of […]
Why a 19th Century Approach to Modern Cyber Security Isn’t Working
Your security teams may know how to build a security platform, but that doesn’t mean they should build one. If you are not a security company, then your security platform may also be an amateur effort, filled with poorly configured components that endanger your data safety.
The Security Dangers of “Lift and Shift” to the Cloud
Cloud and on-premise environments have different security models which can pose a danger when “lifting and shifting” applications
Stuck In the Middle with You – 2019 State of DevOps Report
Puppet’s annual State of DevOps report details the challenges of integrating security and DevOps, and Anitian has some thoughts on this.
The Problem with Compliance
If compliance is not security, then why do it at all?
What is Compliance Automation?
The newest word on the market is Compliance Automation. But what exactly is Compliance Automation? Well, let’s start with what Compliance Automation is NOT.
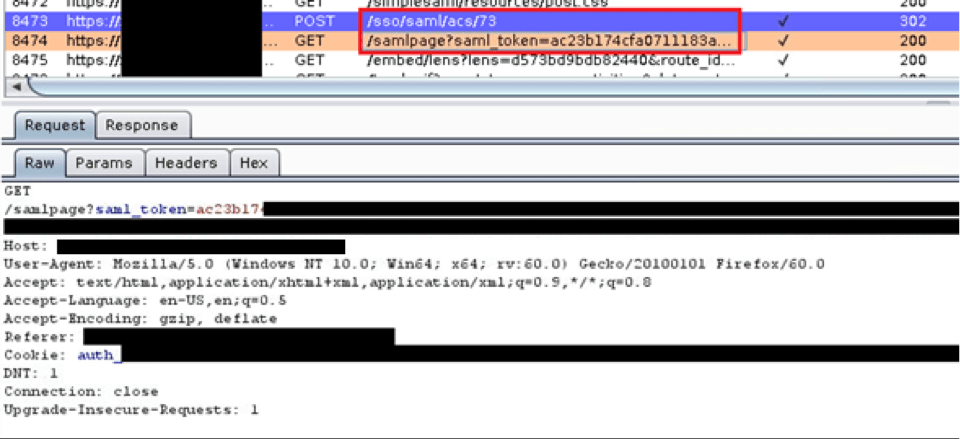
Owning SAML
Exploiting a SAML Implementation and SAML Vulnerability During a recent web application test, I discovered a bug in a Security Assertion Markup Language (SAML) implementation. This bug involved an insecure implementation of a SAML feature combined with a custom authentication mechanism our client developed out of a need to support their customers. With a bit […]
The NGFW is Dead
Let’s get this out of the way: the next-generation firewall (NGFW) is dead. The cause of death: cloud. However, this is not an execution, rather a slow, decline into irrelevance in the face of a more agile competitor. The shroud of death and decay are all around the NGFW products. They are bloated, expensive, and […]
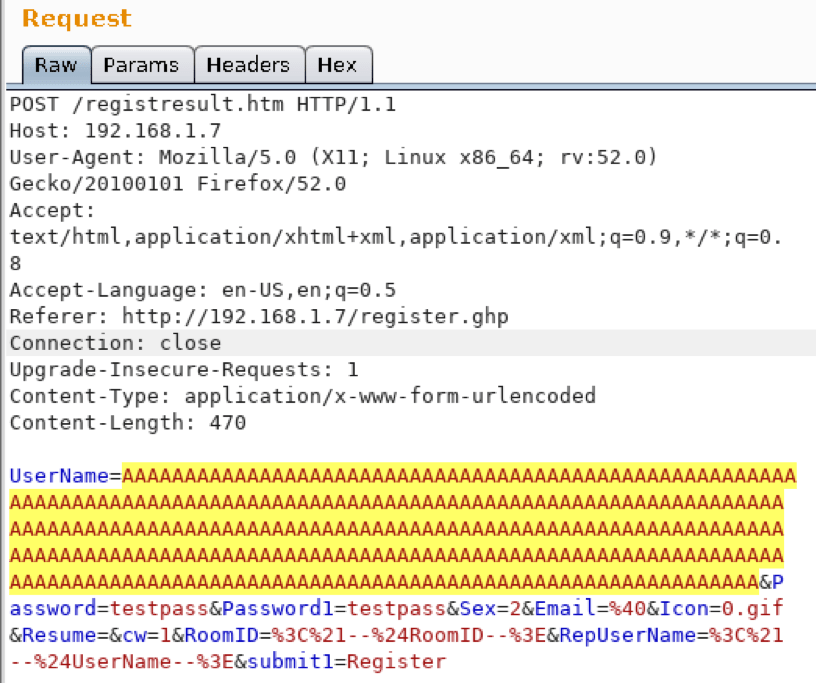
A Study in Exploit Development – Part 2: Taking it to the Next Level
Welcome to Part 2 of this 2-part blog series looking at the details of exploring and validating an exploit! If you liked this series, I bet you’d be interested in our webinar on How to Think Like A Hacker, check it out! Now on to Part 2: Taking it to the Next Level. (Part 1 […]
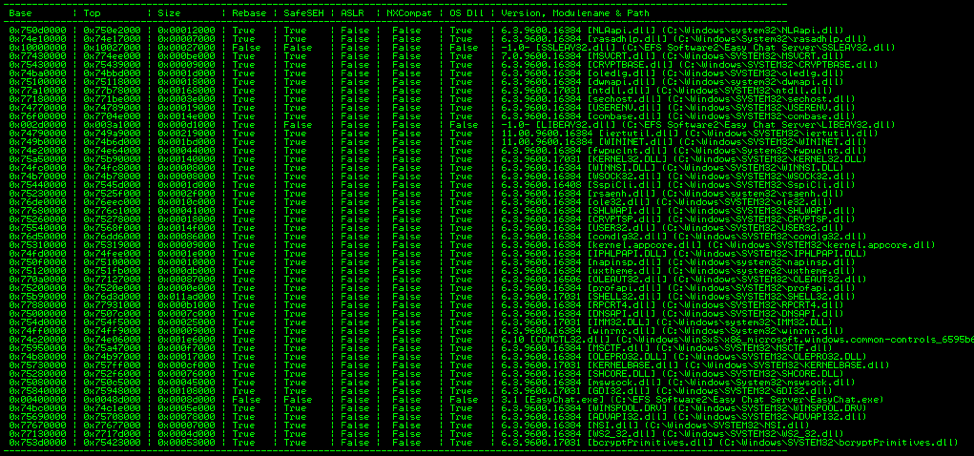
A Study in Exploit Development – Part 1: Setup and Proof of Concept
A Study in Exploit Development: Easychat SEH exploit A typical penetration test involves automated compliance scanning to identify vulnerabilities, followed by a more manual testing process where the tester attempts to validate and exploit those vulnerabilities. Many times, we discover vulnerabilities with publicly available exploits. This can sometimes result in a complete domain compromise. Other […]