All Posts
April 28, 2022
Anomaly Detection Through Machine Learning
The role of a security engineer never stops! Get a technical exploration into how machine learning is changing the game of…
April 21, 2022
Anitian Announces New Accelerate Partner Program to Empower Enterprises to Get Their Applications to the Cloud and Market Quickly and Securely
Pre-engineered, cloud-native SecureCloud platforms combine with a robust partner program to make it easier than ever for channel partners to grow…
April 19, 2022
Anitian Achieves AWS DevOps Competency Status
Anitian achieves Amazon Web Services (AWS) DevOps Competency, validating its technical proficiency and proven customer success specializing in DevSecOps.
March 14, 2022
Cloudy Crystal Gazing: Top 5 Cloud Security Predictions for 2022
We're joined by Dr. Michael J. Savoie to discuss the top 5 cloud security trends and predictions to watch in 2022.
January 26, 2022
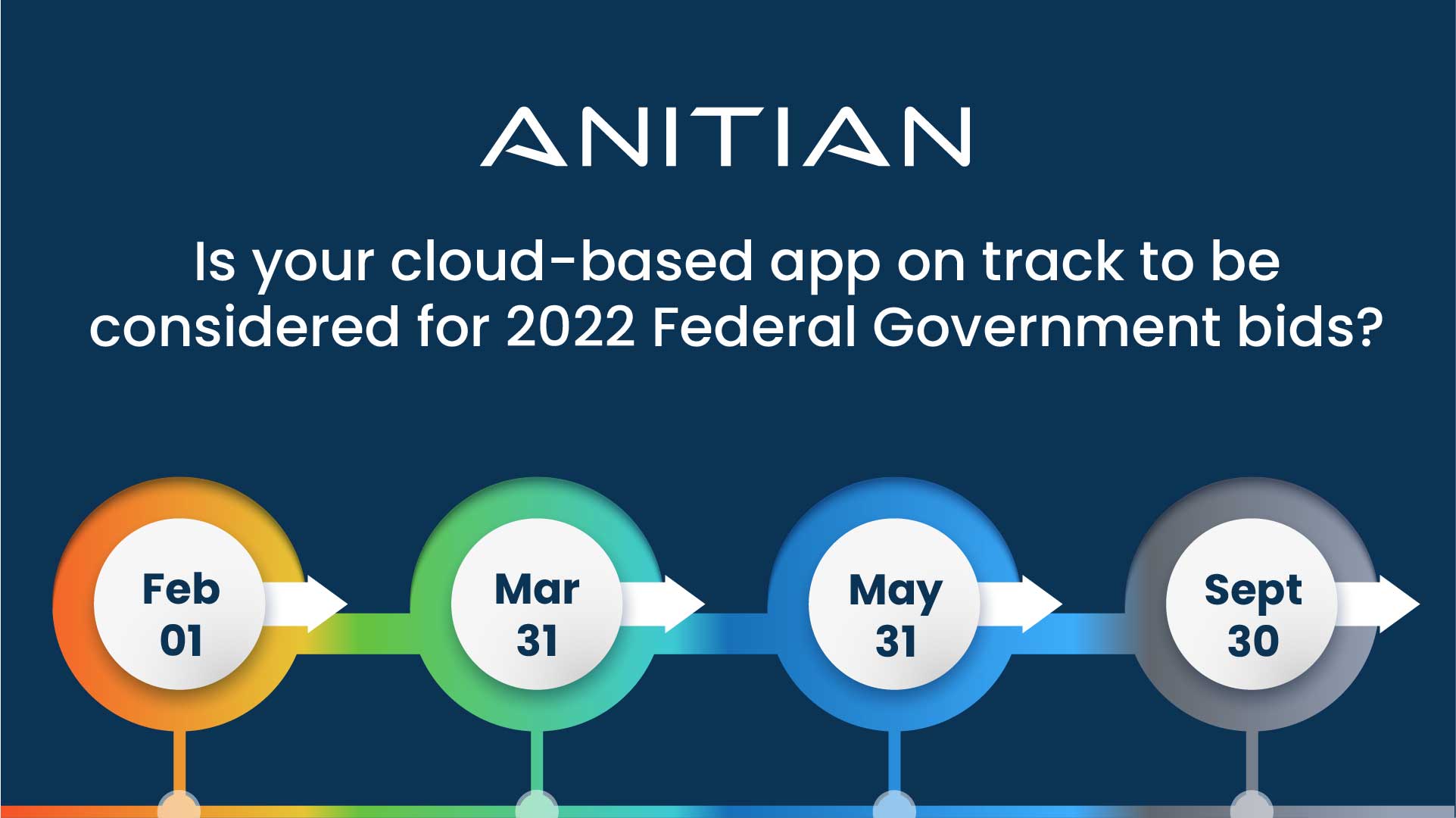
2023 FedRAMP Timeline Milestones: Critical Deadlines Growing Companies Must Know
As cloud-based software vendors seek out new ways to drive revenue for their organizations, many look in the direction of the…
January 20, 2022
What Anitian’s $55M Series B Investment Means to the Future of Cloud Security and Compliance Automation
In a recent report, leading analyst firm Gartner predicted that the Public Cloud Services Market will reach $397.4B this year. In…
January 20, 2022
Anitian Raises $55 Million Series B to Further Transform the Cloud Security and Compliance Automation Industries with Pre-Engineered, Zero Trust Cloud Platforms
Round led by Sageview Capital to fuel Anitian’s growth and product investment to solve the pains of cloud infrastructure security and…
November 8, 2021
Eureka! How Pulumi Brought Sanity to Our DevOps Team
I started out my professional career as a software developer then became a DevOps engineer. (Get it? It’s a joke.) The…
August 27, 2021
Anitian Named a Vendor in Gartner Hype Cycle for Enterprise Architecture
Company also named in the Gartner Hype Cycles for Agile and DevOps, I&O Automation, and IT Risk Management. Link to release…
August 19, 2021
Positioning for Explosive Growth, Anitian Names Former Puppet Executive as New CFO
Julie Crawford brings 20 years of strong financial leadership and experience to support the company’s strategic scale and growth plans. Link…
August 2, 2021
Anitian Named Winner in Prestigious Black Unicorn Awards at Black Hat 2021
Cloud application security and compliance automation leader recognized as potential $1B cybersecurity unicorn by industry-leading judges. Link to release via PR…
July 28, 2021
Anitian Recognized as a Vendor in Three Gartner Hype Cycle Reports
Company named in Hype Cycle for Agile and DevOps, Hype Cycle for I&O Automation, and Hype Cycle for Cyber and IT…
July 20, 2021
Anitian Named a Vendor in Gartner Hype Cycle for Agile and DevOps
Anitian cited as a Sample Vendor in the Continuous Compliance Automation (CCA) category, as DevOps and DevSecOps adoption grows. Link to…
July 13, 2021
Infographic: How Anitian Cloud Security & Compliance Automation Delivers on the Cybersecurity Executive Order
On May 12, 2021, President Joe Biden signed an Executive Order (EO) on Improving the Nation’s Cybersecurity, indicating a future increase of regulatory…
July 12, 2021
Cloud Security Automation: The Fastest Path to Zero Trust
I can still hear the dismissive calls of it being “just another security buzz word.” That was two years ago while advocating the importance of…
July 1, 2021
Anitian Joins Microsoft Intelligent Security Association (MISA) & Expands Microsoft Collaboration for Azure Customers
Just months after launching our Compliance Automation Platform on Microsoft Azure, Anitian is honored to announce that we have joined the…