All Posts
May 16, 2017
Hardening iOS
Hardening the Apple iPhone and iPad is easier thanks to a new benchmark from the Center on Internet Security.
April 19, 2017
Avaya Hack
Discovery of Avaya servers in an network is consistently as target rich environment for hacking.
March 2, 2017
Red Team Penetration Testing – Fallout (Part 3 of 3)
What can we learn from our recent red team penetration testing results about the state of information security in 2017.
March 1, 2017
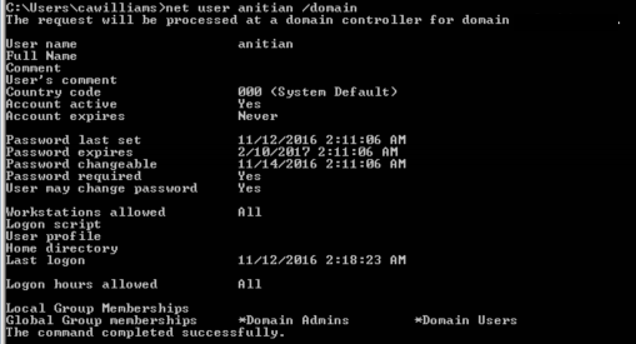
Red Team Penetration Testing – Going All the Way (Part 2 of 3)
The further chronicles of Anitian's red team testing. Armed with a single stolen user account, we completely compromise a corporate network.
February 27, 2017
Red Team Penetration Testing – Anything Goes (Part 1 of 3)
Chronicle of a recent red team penetration test from Anitian's Ring.Zer0 team that shows how a dedicated attacker can bypass even…
January 23, 2017
Goodbye Yellow Brick VAR
Oh we've finally found where our future lies, beyond the yellow brick VAR.
November 15, 2016
The Gilfoyle Problem
We are going on a Vision Quest to explore our Gilfoyle Problem in IT and cybersecurity.
October 27, 2016
PCI DSS 3.2 Multi-Factor Authentication Clash
Multi-factor authentication (MFA) is a tried and true technology that rarely incites debate. How then did MFA became a hotly debated…
September 20, 2016
More Hacking SQL Servers Without a Password
We return to hacking SQL servers, with a whole new script that automates the attack.
August 2, 2016
Future SOC
People passively monitoring alerts is not an effective SOC strategy. We need a Future SOC.
May 5, 2016
Nuke the Checkbox Audit from Orbit, or Alienate the Millennials
Millennials have a high affinity for authentic leadership. That means your information security program must also be authentic. Purging the practice…
April 21, 2016
Hacking Nagios: The Importance of System Hardening
A recent penetration test uncovered some serious vulnerabilities in a Nagios deployment and served as a reminder that system hardening is…
February 5, 2016
Hacking Microsoft SQL Server Without a Password
Using a Man in the Middle (MITM) style attack and some packet manipulation, you can hack any Microsoft SQL Server and…
January 6, 2016
Digging Deeper – Striking Gold in Penetration Testing
Sometimes automated scanners cannot detect subtle vulnerabilities embedded deep inside scripts. It pays to dig a little deeper to strike vulnerability…
October 20, 2015
Illusions of Information Security – The Struggle for Truth
In October 1995, I finally found my calling. What I found was SQL Injection, perhaps the most prevalent web site hack…
August 20, 2015
Anatomy of a Hack: Cross-Site Request Forgery (CSRF)
Cross-Site Request Forgery is a common vulnerability that many web application scanners can miss. In this real-world example, Anitian demonstrates how…