All Posts
October 13, 2018
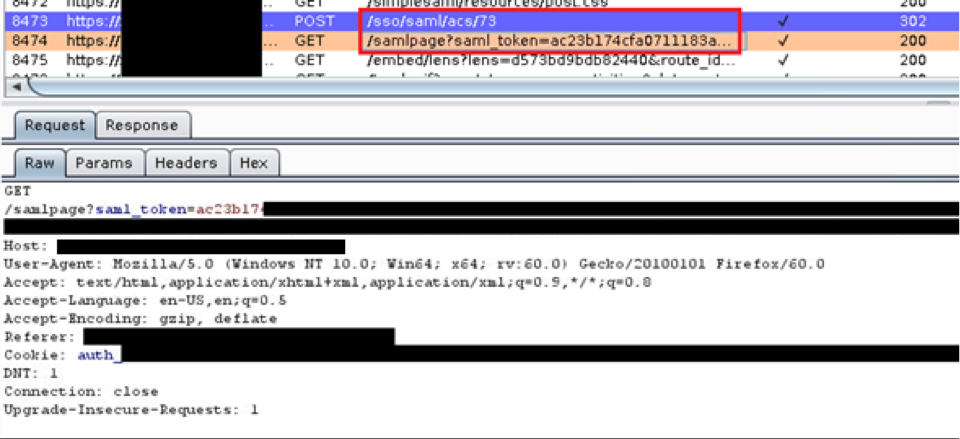
Owning SAML
Exploiting a SAML Implementation and SAML Vulnerability During a recent web application test, I discovered a bug in a Security Assertion…
August 10, 2018
The NGFW is Dead
Let’s get this out of the way: the next-generation firewall (NGFW) is dead. The cause of death: cloud. However, this is…
April 2, 2018
A Study in Exploit Development – Part 2: Taking it to the Next Level
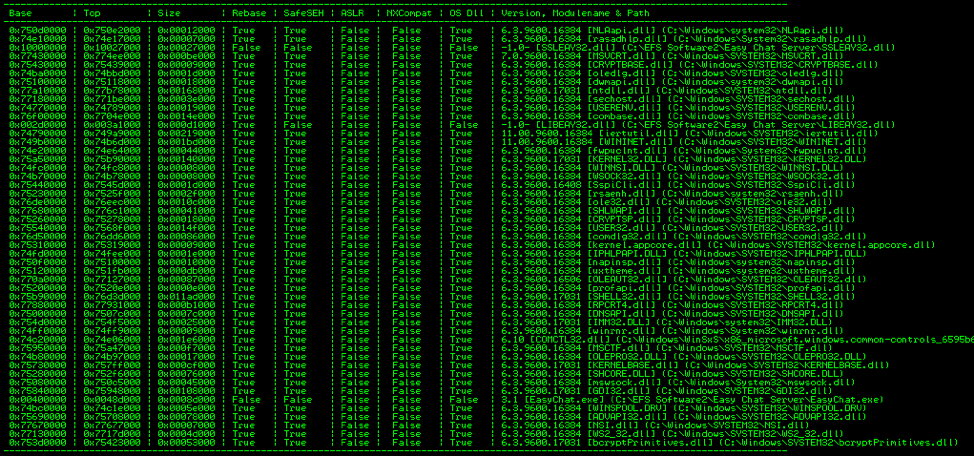
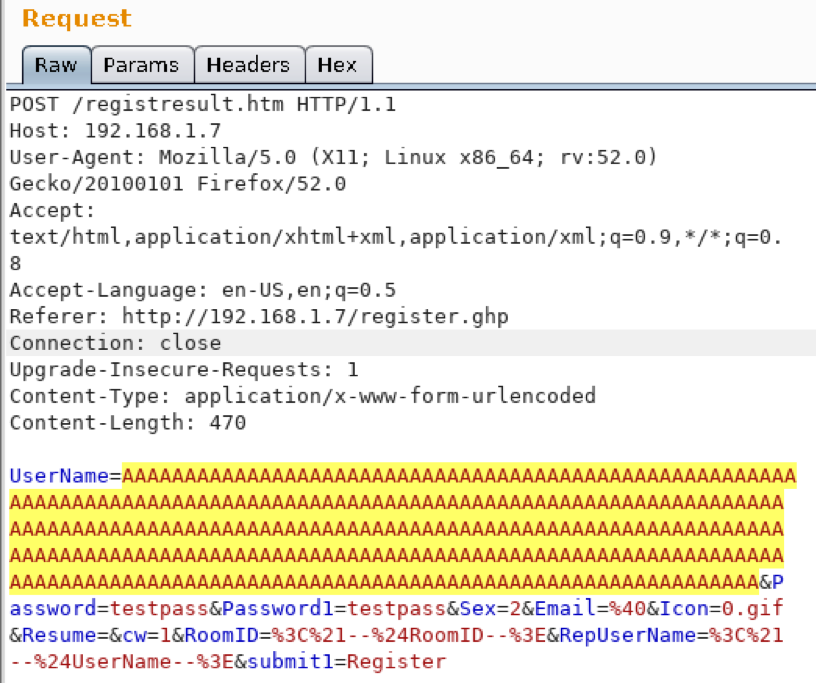
Welcome to Part 2 of this 2-part blog series looking at the details of exploring and validating an exploit! If you…
March 27, 2018
A Study in Exploit Development – Part 1: Setup and Proof of Concept
A Study in Exploit Development: Easychat SEH exploit A typical penetration test involves automated compliance scanning to identify vulnerabilities, followed by…
March 5, 2018
The Top Five SOC 2 Compliance Questions Answered
SOC2 compliance is a must-have for SaaS companies. Anitian's VisionPath compliance team looks at your road to SOC2 compliance.
February 23, 2018
How to Make PCI Compliance a Little Easier for Everyone
Before we begin, there’s one thing to make very, very clear: You cannot outsource ALL compliance! I do not care what…
February 6, 2018
The Human Firewall is a Lie
It is delusional to think we can deprogram millennia of human evolution because information security is difficult. The human firewall is…
November 30, 2017
Ulterius Zero Day Disclosure
How Anitian discovered a zero day vulnerability in the Ulterius remote access software, and wrote an automated exploit tool.
November 30, 2017
Ulterius Zero Day Disclosure
How Anitian discovered a zero day vulnerability in the Ulterius remote access software, and wrote an automated exploit tool.
November 15, 2017
GDPR is Coming
GDPR has rapidly devolved into a touchstone for everything from vendor FUD to political frothing. It has been hailed as a huge…
October 26, 2017
Webinar Video: PCI Compliance for AWS Cloud
Anitian wrote the book on PCI Compliance for AWS (along with the team at AWS). How do you make AWS environments…
September 5, 2017
What’s New in NIST 800-53 R5
The new NIST 900-53 Revision 5 is out, and we look at the changes.
August 10, 2017
ISO 27001 – Part 3 – The Audit
ISO 27001 audits are not like other kinds of security assessments
August 9, 2017
ISO 27001 – Part Two – Building an ISMS
Learn the six steps to building an ISO 27001 ISMS
August 8, 2017
ISO 27001 Compliance – Part 1 – The Fundamentals
ISO 27001 compliance is rapidly become a model standard for organizations wishing to demonstrate security diligence in a global market.
June 12, 2017
The Road to SOC2
SOC2 compliance is a must-have for SaaS companies. Anitian's VisionPath compliance team looks at your road to SOC2 compliance.