Cloud and on-premise environments have different security models which can pose a danger when “lifting and shifting” applications
Owning SAML
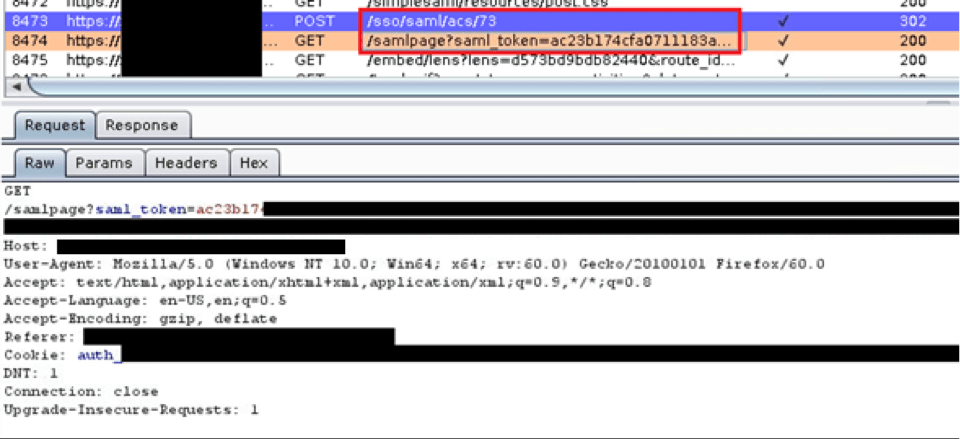
Exploiting a SAML Implementation and SAML Vulnerability During a recent web application test, I discovered a bug in a Security Assertion Markup Language (SAML) implementation. This bug involved an insecure implementation of a SAML feature combined with a custom authentication mechanism our client developed out of a need to support their customers. With a bit […]
A Study in Exploit Development – Part 2: Taking it to the Next Level
Welcome to Part 2 of this 2-part blog series looking at the details of exploring and validating an exploit! If you liked this series, I bet you’d be interested in our webinar on How to Think Like A Hacker, check it out! Now on to Part 2: Taking it to the Next Level. (Part 1 […]
A Study in Exploit Development – Part 1: Setup and Proof of Concept
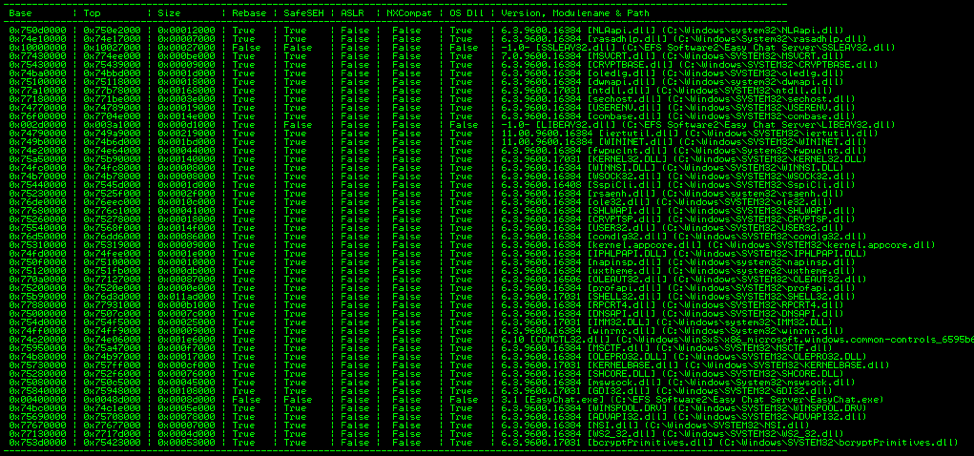
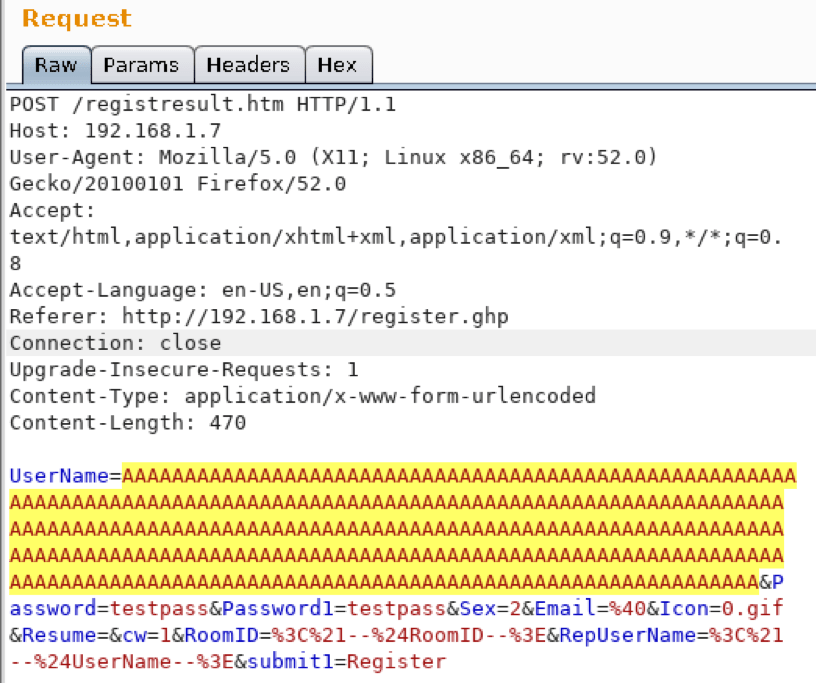
A Study in Exploit Development: Easychat SEH exploit A typical penetration test involves automated compliance scanning to identify vulnerabilities, followed by a more manual testing process where the tester attempts to validate and exploit those vulnerabilities. Many times, we discover vulnerabilities with publicly available exploits. This can sometimes result in a complete domain compromise. Other […]
Ulterius Zero Day Disclosure
How Anitian discovered a zero day vulnerability in the Ulterius remote access software, and wrote an automated exploit tool.
Ulterius Zero Day Disclosure
How Anitian discovered a zero day vulnerability in the Ulterius remote access software, and wrote an automated exploit tool.
Anatomy of a Hack: Cross-Site Request Forgery (CSRF)
Cross-Site Request Forgery is a common vulnerability that many web application scanners can miss. In this real-world example, Anitian demonstrates how multiple CSRF attacks can be chained together to create a more serious attack.
Enough with the Stunt Hacking
The time has come for the information security profession to reject stunt hacking such as the sensational car hacks that Charlie Miller and Chris Valasek performed.
Is badBIOS for Real?
Is badBIOS a real threat? Maybe not, but the origin of this threat could be a very real problem.