Let’s get this out of the way: the next-generation firewall (NGFW) is dead. The cause of death: cloud.
However, this is not an execution, rather a slow, decline into irrelevance in the face of a more agile competitor. The shroud of death and decay are all around the NGFW products. They are bloated, expensive, and ineffective. They command irrational emotional fetishism among their users who consistently overemphasize their importance. In ten years, the NGFW will be reduced to a glorified router.
However, no need to panic. You still have time to make arrangements for life after the NGFW.
What is an NGFW Security Tool?
The NGFW (or UTM if you prefer that parlance) has ruled over security for about 10 years. NGFW grew out of the merging of firewalls, intrusion prevention systems, and web proxies to become the Swiss Army Knife of security. Everybody has an NGFW, and of course the one you bought is the best (insert eye-rolling meme here).
The NGFW is not only the central technology in many security programs, for some people the NGFW *is* the security program. It is not uncommon for a CISO, when asked about their security program, to begin their answer with “well, we have Palo Alto’s at the perimeter…” That is not a security program! This overemphasis on the NGFW means this death will not come easy for those who have built an entire career around this technology.
However, as Tyler says, you are not your NGFW (or your khakis for that matter). It is time to evolve.
Four reasons why NGFW technology is dying
Before you fly off the handle, or any other car part for that matter, let’s explore the four reasons the NGFW is dying:
- The network perimeter is gone
- NGFW’s are not designed for cloud architectures
- Cloud providers are (or will) offer the same capabilities at a fraction of the cost
- The NGFW is not effective
These reasons are borne out of observations of trends, specifically where the cloud is concerned.
1. NGFW network perimeter is gone
Modern organizations have, at best, a flimsy network perimeter. As companies move more data and workloads to the cloud and SaaS providers, the “perimeter” consequently extends to those providers. Add a growing remote worker population to this and whatever soft perimeter existed before, becomes completely ephemeral. Without a clear perimeter, each individual laptop, phone, and IoT device *is* the perimeter. Likewise, the classic core data center is disappearing as well, for all the same reasons.
This is the driving force behind cloud endpoint companies, like Zscaler. At RSA a few years ago, Zscaler had a supremely entertaining booth where you could take a sledgehammer to NGFW hardware like Palo Altos and CheckPoints. I ashamed to admit, but I whacked a few Cisco ASAs.
At the time, I thought this was merely a marketing gimmick. However, Zscaler was having a Howard Beale moment: hardware is meaningless when your workforce, data, and systems are distributed throughout the cloud, homes, and coffee shops.
Zscaler represents this shift from large racks of network gear to a cloud provider that aggregates connections and data in the cloud and provides all the security scanning, filtering, and protections you need. When you have critical business systems in the cloud or SaaS providers, that giant Palo Alto or Checkpoint you bought is utterly meaningless to their security. The on-premise NGFW is relegated to a basic connectivity device at the office.
2. NGFW not designed for cloud architecture
When you move data and workloads into the cloud, the whole concept of networking mutates. Cloud providers, like AWS and Azure, are software-defined networks. All traffic and connectivity are virtualized and abstracted from the actual wires and routers. This is even more pronounced with SaaS providers, where there is no network at all.
Furthermore, software-based networking does not have the constraints of traditional networks. Traditional “three-tier” networks aggregated and concentrated access because it was efficient. However, it is constraining. All traffic must go back to central routes and NGFWs for access.
In the cloud, this is unnecessary. Traffic goes directly where it must go. For example, if you have application servers and database servers, you do not connect them through a router, rather you peer them together. Since you do not control the underlying physical connectivity, there is no reason to route back to a central point.
Peering provides extremely granular and dynamic access control. Not only can you control network, application, and user-level access but that access can be granted and revoked in an automated manner based on specific conditions or triggers. Using cloud management solutions, you can constantly audit those controls, and revoke them if any access violates company policies. This level of control is nearly impossible in a traditional, hardware network.
Moreover, when native cloud services are used, such as AWS’s identity and access management (IAM) or Azure’s hosted Active Directory, there is no actual server to connect to. Rather, you peer your VPCs or hosts to the service itself.
Peering simplifies the network, without reducing any of the access control. In a sense, you do not need to network at all.
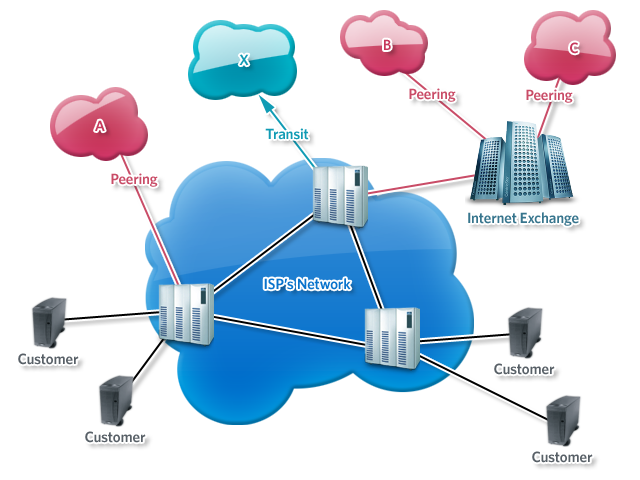
It is clumsy (and even impossible in some cases) to put a NGFW between cloud-hosted systems and native services. While all of the NGFW makers offer cloud versions of their products, more often than not, these are relegated to VPN connectors. Whatever security functions they provide are easily supplanted with other capabilities.
Consequently, the lack of NGFWs in the cloud has seen a subsequent rise in host-based security solutions. Companies like Trend Micro understood this years ago, and began releasing cloud-centric versions of their products that offer all the NGFW capabilities, on a host-based platform. Furthermore, when you automate the deployment and configuration of those endpoints (which is exactly what we do in our Sherlock Managed Detection and Response services) then you can uniformly enforce security on every host in the environment.
3. Cloud provider offer NGFW capabilities built in
Cloud platforms, namely AWS and Azure, offer (or will offer soon) NGFW capabilities. No large piece of equipment (or virtual image) necessary.
With the release of Guard Duty from AWS, it is blatantly obvious where AWS is headed. AWS wants to own not only your compute workloads, but all the infrastructure as well.
Guard Duty is a native AWS application that offers intrusion detection monitoring Traditional intrusion detection (prevention) systems (IDS/IPS) are nearly impossible to deploy into cloud networks because you cannot see the full network packet. The abstraction of the network, also means you cannot sniff traffic.
In the next few years, AWS and Azure will, in some manner, offer all the capabilities of a NGFW as native products. This is a logical maturation for any Infrastructure as a Service provider. Also, as adoption of native NGFW capabilities increases, cost will plummet. This will further erode the value of the traditional NGFW.
4. NGFW is not effective
The final reason the NGFW is dying is perhaps the most obvious – NGFWs are ineffective. Every organization that has reported a megabreach had a NGFW. And those NGFWs did nothing (or little) to stop the breach.
In all fairness, it is not the NGFW technology that is the root cause here. Rather, it is a cumulative set of architectural and organizational issues that conspire to further diminish the value of a NGFW.
What makes NGFW’s not secure?
- There are numerous ways to get around NGFWs, using mobile networks or physical devices.
- Trusted third parties, who demand unrestricted access, often bypass all NGFW security.
- The people managing the NGFW lack the authority to enforce rules for fear of “blocking legitimate traffic.”
- Practices to monitor and respond to the NGFW for alerts are ineffective because:
- Alert management tools (like a SIEM) are complex and time-consuming to administer
- Lack of talented security staff
- An overwhelming number of alerts
- A passive-aggressive, conflict-avoidance culture that discourages reporting an incident, since it will invite scrutiny
That last item is perhaps the most destructive and prevalent. Many, large organizations cultivate a culture that is intolerant to normal human error. This is particularly destructive for information security. Weak leaders place utterly unrealistic expectations and constraints on information security practitioners. There is an expectation that they know everything, miss nothing, and will be severely punished if anything bad happens. Nearly every breach that has happened in the past 10 years revealed this Culture of Breach (which we wrote about in another blog.) Enterprise cloud security should be a focal point for every organization.
If not, this creates a toxic culture where security people are given tremendous responsibility, but none of the authority to actually fulfill that responsibility. This is also why many of them cling to their NGFW like Gollum to the Ring. Lording over a big NGFW is the only power they have.
However, they are discouraged from ever reporting any attack, since the bad leaders (with ludicrous expectations) will blame them for the alerts. This is a potent negative feedback loop, that many NGFW vendors feed, because it gets those ineffectual security people to buy larger, more powerful boxes.
And this is why we need the NGFW to die. Death begets change.
NGFW tools will evolve

About now, you are either depressed, because you agree with my assessment of the NGFW, or you are angry and figuring out what personal flaws I have so you can attack me.
Here, I will help you: I am angry, fat, and swear a lot. I also spend way too much money on cars, and routinely say insulting things to people.
I am sure you can belittle me with one or all of those.
However, before you go rip that Fortinet from its FortiBolts, chill out. The NGFW is not dying a quick death. All that money you spent with that Palo Alto VAR is not immediately going to waste. This death is slow. The NGFW will not die completely. It will change.
In five to ten years, the NGFW will be more of a cloud connectivity appliance. You are already seeing the first vestages of this with Fortinet and Palo Alto (who just bought Evident.IO) It will continue to control access. But, you will manage it more like you manage a SaaS subscription. Also, secure, controlled connectivity to AWS, Azure, Salesforce, and such will be baked right into the platform.
Also, AWS and Azure will have their own NGFW-like services, meaning you can ditch your on-premise NGFW entirely, and use inexpensive routers. This makes services like Zscaler will make more sense, than a big iron box of wires.
The bigger movement happening here is the growing irrelevance of on-premise anything. NGFW is really part of a much larger trend. As companies move more and more workloads into the cloud, all those racks of gear become less and less relevant.
In 2012, people were fighting to keep their Exchange services on-premise. Here it is 6 years later and the notion of having an on-premise Exchange server is laughable. In 6-10 years, the notion of having a giant, $100,000 core NGFW will seem equally laughable. Also, your VARs are dying, but that too is another blog.
How to prepare to transition from an NGFW solution
If you want to prepare for the demise of the NGFW, the answer is all over your Azure or AWS console. While this is not a comprehensive list of things you can do to prepare, it will get you going down the path.
- Refocus on endpoint security, specifically solutions that offer NGFW functions at the endpoint
- If you have a distributed workforce, then you should have companies like Zscaler on your radar
- Move those workloads into the cloud, the sooner they better
- Cloud security is not the same as on-premise security. This topic is outside the scope of this blog, but suffice to say, you cannot just forklift all your on-premise gear into the cloud and expect it all to work
- Risk management and personal development should be at the core of your security program, not technology
- SIEM technology is more important in the cloud. You need data to drive decisions. This too is a whole different blog.
As you can see, once you open the doorway of a post-NGFW world, things change, significantly. The more cloud-focused your team the better suited you will be for this change. Anitian SecureCloud for compliance automation is simply the fastest path to PCI, ISO 27001, and FedRAMP compliance for your enterprise.
Conclusion
In 2003, when Richard Stiennon declared IDS was dead, he was hounded for years. It is normal for people to react to a new idea with scorn, anger, and childish harassment. Stiennon was correct, of course. The IDS was a dying tech. For those of us who watch the security industry night and day, these trends are obvious. Look around, the cloud is gobbling up everything, and like it or not, the NGFW is its next victim.
And remember, death is not the end. It is the beginning of something new (cue dramatic music.)
Not only is the NGFW on the way out, the “human firewall” isn’t doing so well either – read more here.




One thought on “The NGFW is Dead”
May be you are right but we are using sangfor’s firewall NGAF and i must say its a great firewall in my opinion.